OpenID Connect
The E-Ident service uses the OpenID Connect (OIDC) as one of two possible identification protocols. This page outlines the identification process, the identification parameters and the ID Token.
OpenID Connect identification
Identification in E-Ident can be done using the OIDC protocol and the implementation supports the Authorization Code Flow with the optional PKCE and CIBA flows. The figure below illustrates the identification sequence when using OIDC.
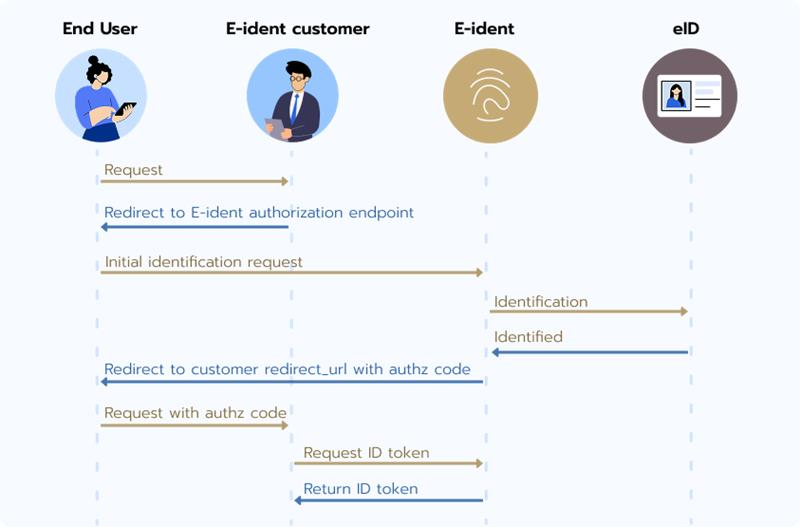
The end user accesses the E-Ident customer site with a request to log on.
The end user browser is redirected to E-Ident to begin identification. Sample identification request: https://www.ident-preprod1.nets.eu/its/index.html?client_id= <client_id>&response_type=code&redirect_uri=<redirect_uri>&scope=openid+ssn&state=2017-06-12-15.12.43.345354&nonce=386145d332342
Read more about the mandatory and optional parameters below.End user identification is initiated towards a selected eID. The end user supplies his/her credentials.
E-Ident redirects the end user to the E-Ident customer's redirect_uri by appending the query string
?code=<authorization code>. Similarily, the state parameter, as sent by the customer, is also appended to the redirect_uri.The E-Ident customer requests an ID Token based on the authorization code. Successive token requests with the same authorization code (code) will result in error and invalidation of previously accessed tokens.
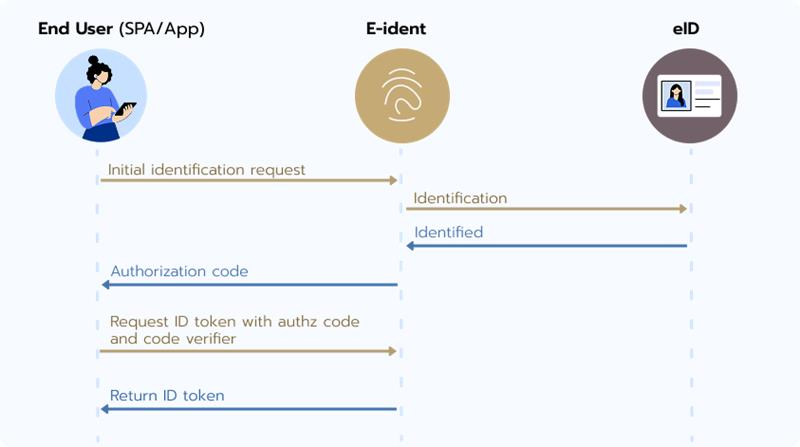
PKCE flow
The Proof Key for Code Exchange (PKCE) flow allows Single Page Application (SPA) and native apps to retrieve the ID token directly in a secure way without revealing the password and not through a backend call. The flow is optional and works likes this:
Customers must generate a code_verifier value
Optionally the customers transforms the code_verifier value and sends it as a code_challenge to the E-Ident service along with the identification request. The customers may also optionally send the code_challenge_method (SHA-256 or plain) along with the identification request.
After authentication, the code_verifier is sent when retrieving the token. The E-Ident service will verify the code_verifier against the original challenge, using the specified method (SHA-256 or plain).
CIBA flow
Standard authentication using OIDC relies on the user agent (user's browser) first access the OIDC provider to initiate the session. The response from the provider is a web UI that guides the user through the authentication sequence.
The Client Initiated Backchannel Authentication (CIBA) flow enables authentication sessions to be initiated and processed in a different channel than the browser through the E-Ident web UI.
The following diagram illustrates a CIBA flow use case:
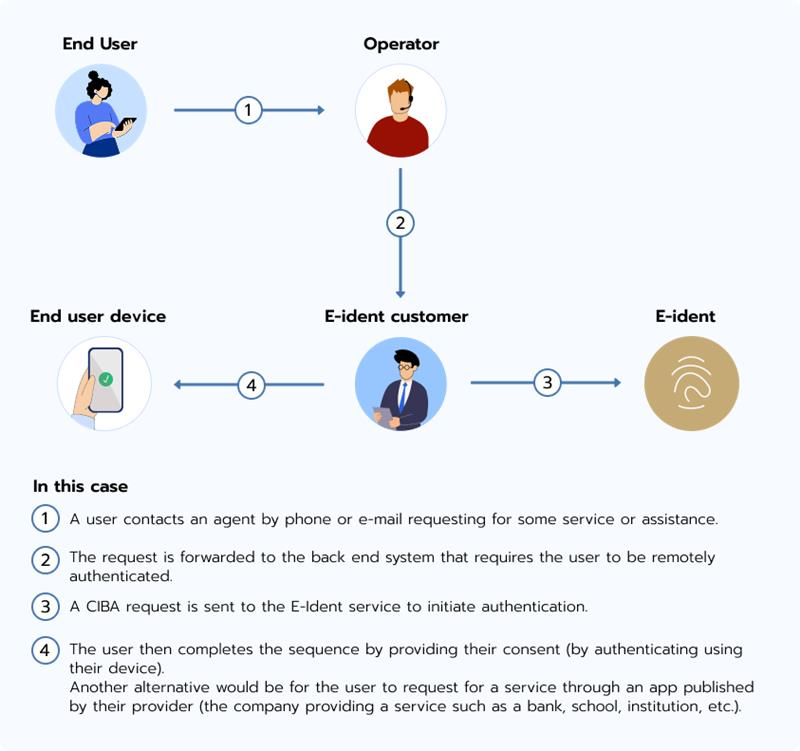
After authentication in the user device, the service provider in this use case can retrieve the ID token from the E-Ident service.
Implementation
To implement the backchannel flow, customers will need to follow the following sequence:
call the CIBA endpoint to start a new authentication transaction. See CIBA specific identification parameters below.
use the response to start user authentication (user consent)
wait for the user complete(alternatively, poll the server for updates)
retrieve the ID token
Requesting for a CIBA transaction
curl -kiSs \
https://www.ident-preprod1.nets.eu/oidc/ciba \
-H 'Authorization: Basic <<Base64Encoded username:password>>' \
-d scope=openid \
-d amr_values=passport_readerUpon success, the server will respond with a unique ID that is bound to the new session
{"auth_req_id":"c69597e96f5a4dcc970ec38e5a85a4c3","interval":5,"expires_in":600}The auth_req_id is a session ID that can be provided to the authentication app to facilitate consent confirmation (authentication).
Requesting for CIBA transaction with login hint and binding message
When starting a CIBA transaction with IN Groupe ID verifier, the following optional parameters ntdr-doc-types and ntdr-app-doclist can be sent through binding_message. ntdr-doc-types parameter accepts the following values: I, P, D and V. These alphabets mean ID cards, Passport booklets, Driver's license and Viza/crew credentials respectively. ntdr-app-doclist parameter accepts boolean value indicating whether the document type selection page will be shown to the user.
For IN Groupe ID Verifier, binding_message will accept value in JSON format.
A valid JSON format for binding_message is:
{
"ntdr-doc-types": "<I, V, D, P>" (multiple values, with comma separation, are allowed),
"ntdr-app-doclist": "<true/false>"
}
BankID (NO)
When starting a CIBA transaction with Norwegian BankID, it's required to specify the end user's identity. This is done by passing the login_hint parameter with the correct data depending on the authentication method. It is also mandatory to pass acr value with amr_values separated by semicolon. Acr_value is optional.
curl -kiSs \
https://www.ident-preprod1.nets.eu/oidc/ciba \
-H 'Authorization: Basic <<Base64Encoded username:password>>' \
-d scope=openid \
-d login_hint=<loginHint> \
-d amr_values=<<URL encoded no_bankid;urn:bankid:bis,urn:bankid:bih>> \
-d acr_values=<<URL encoded urn:eident:acrp:level:substantial,urn:eident:acrp:level:low>>Upon success, the server will respond with a unique ID and binding_message which can be used in authentication
{
"auth_req_id": " b1dc0ec3d1f4496b8f5396b042cbeff1",
"interval": 2,
"binding_message": "Raggete knott",
"expires_in": 600
}After this user can start polling and collect the idToken.
BankID (SE)
For BankID (SE), it's optional to specify login_hint. If login_hint is provided, then that will be used to exclude other user's SSN than the provided SSN.
The binding message will accept values in text or JSON format which will appear on the end user's device. BankID SE supports two ways of CIBA authentication depending on the amr_values parameter.
se_bankid
The “amr_values" can be passed as “se_bankid" which will return auth_req_id and autostart_token. Use this token to launch the app. Please refer https://www.bankid.com/en/utvecklare/guider/teknisk-integrationsguide/programstart for technical details.
se_bankid:mobile
The “amr_values" can also be passed as “se_bankid:mobile" which will return one additional token called qr_data, use this qr_data to create animated QR code which can be scanned by BankID app. Once the first QR code is created then the polling should be done every second for token endpoint. The qr_data will be returned in every polling which can be used to update the animated QR code every second.o
curl -kiSs \
https://www.ident-preprod1.nets.eu/oidc/ciba \
-H 'Authorization: Basic <<Base64Encoded username:password>>' \
-d scope=openid \
-d amr_values=se_bankid:mobile
Upon success, the server will respond with a unique ID and qr_data that is bound to the new session
{
"auth_req_id": "5be667afc6624d938a370d70b79d1c44",
"interval": 2,
"qr_data": "bankid.553399f8-8e65-45b5-9b83-d17d2631d88a.0.f6a74ceaafbf31d5274b8b65ffe116c30eace8457870e7aa15beaa7842594efa",
"expires_in": 600,
"autostart_token": "753b0e6b-3342-4fc1-90de-657dc8e39d89"
}
Start polling for below endpoint
curl -kiSs \
https://www.ident-preprod1.nets.eu/oidc/token \
-H 'Authorization: Basic <<Base64Encoded username:password>>' \
-d grant_type=urn:openid:params:grant-type:ciba \
-d auth_req_id=5be667afc6624d938a370d70b79d1c44
Upon success, the server will respond with a qr_data
{
"error": "authorization_pending",
"error_description": "Consent confirmation is still pending",
"qr_data": "bankid.80cc06dc-2686-4d4f-ad0b-73df09d76d80.11.64e6835d7bba6e9389449a4e7fca5e2aa9d56e01bb5c0ac5f014d16317a7d3b1"
}
A QR code generation library can be used to produce the QR code in the preferred size.
A valid JSON format for binding_message is-
{
“transactiontext": “base64encoded (content from merchant)",
“transactiontext_type": “<text/markdown>"
}
TrustID
When starting a CIBA transaction with TrustID, it's optional to specify the end user's identity. This is done by passing the login_hint parameter with the correct data depending on the authentication method. The binding_message parameter accepts JSON format which have data for message which will appear on end user's device, request type, user status etc.
A valid JSON format for binding_message is
C
{
"requestType": "<provisioning/authentication>",
"appId": "<appId value>",
"bindingMessage": "<content from merchant>",
"userStatus":"<active/locked >"
}
For more information go to TrustID.
MitID
When starting a CIBA transaction with MitID, it's required to specify the end user's identity. This is done by passing the login_hint parameter with the correct data. login_hint can be a CPR or a UUID. The binding_message parameter is used to specify the text that will appear on the end user's device.
curl -kiSs \
https://www.ident-preprod1.nets.eu/oidc/ciba \
-H 'Authorization: Basic <<Base64Encoded username:password>>' \
-d scope=openid \
-d amr_values=mitid \
-d login_hint=<login hint> \
-d binding_message=<pass your message here>Retrieving the CIBA ID token
curl -kiSs \
https://www.ident-preprod1.nets.eu/oidc/token \
-H "Authorization: Basic <<Base64Encoded username:password>>" \
-d grant_type=urn:openid:params:grant-type:ciba \
-d auth_req_id=c69597e96f5a4dcc970ec38e5a85a4c3The following E-Ident providers currently support the CIBA flow:
BankID (NO)
BankID (SE)
IN Groupe ID Verifier
TrustID
MitID
Identification request parameters
The different identification request parameters are divided in these sections:
Mandatory
Name | Description | Value |
|---|---|---|
aud | The Identity Provider the request is intended for. This is a mandatory parameter but only in a signed request. | E-Ident's Issuer Identifier URL: Customer test: https://www.ident-preprod1.nets.eu/oidc Production: https://www.e-ident.nets.eu/oidc |
client_id | The customer identifier given upon registration. Often referred to as MID or merchant identifier. This is not the same as the MerchantID. | MID |
iss | The client that created the request. This is a mandatory parameter but only in a signed request. | The customer identifier given upon registration |
redirect_uri | A URL to the customer resource that will process OIDC claims after authentication. One or more redirect_uri must be registered on the customer configuration. The URL the end user is going to be returned to must be set in the redirect_uri parameter when the customer initiates an identification. | Customer redirect uri as registered in E-Ident. |
response_type | OAuth 2.0 Response Type value that determines the authorization processing flow to be used, including what parameters are returned from the endpoints used. When using the Authorization Code Flow, this value is code. | code |
scope | Scopes are used to retrieve the claims that are grouped in the below table. The optional values are custome scopes in E-Ident. None, one or more can be requested at the same time. | Mandatory scope: openid Space-separated list. |
state Opaque value used to maintain state between the request and the call back. Typically, Cross-Site Request Forgery (CSRF, XSRF) mitigation is done by cryptographically binding the value of this parameter with a browser cookie. The customer should check the value of this parameter against the value returned by E-Ident after identification. If it does not match, error should be thrown. Unique random value | Opaque value used to maintain state between the request and the call back. Typically, Cross-Site Request Forgery (CSRF, XSRF) mitigation is done by cryptographically binding the value of this parameter with a browser cookie. The customer should check the value of this parameter against the value returned by E-Ident after identification. If it does not match, error should be thrown. Unique random value | Opaque value used to maintain state between the request and the call back. Typically, Cross-Site Request Forgery (CSRF, XSRF) mitigation is done by cryptographically binding the value of this parameter with a browser cookie. The customer should check the value of this parameter against the value returned by E-Ident after identification. If it does not match, error should be thrown. Unique random value |
Optional
Name | Description | Value |
|---|---|---|
additional_info | The additional info parameter can be used by any customer to enter their own information. The parameter value will be returned as it was entered in the corresponding claim in the ID Token or attribute in the SAML assertion. In addition, the information is added to E-Ident statistics and may be returned to the customers as part of statistics. The last part must be agreed with IN Groupe in each case. | Format: [A-Za-z0-9_\-åøæÅØÆ]{0,50} Max length: 50 characters |
amr_values | Requested Authentication Method Reference values. Only for BankID (NO) and Verimi this parameter contains 2 values separated by semicolon ( ; ). First value- Space-separated string that specifies the "amr" values that the Authorization Server is being requested to use for processing this Authentication Request, with the values appearing in order of preference. The authentication methods used for the authentication performed are returned as the amr Claim Value. This parameter is equivalent to the forcepkivendor parameter of SAML identification. Second value- Comma-separated string, this will give access to control the authentication method for a specific identification. The actual used authentication method will be returned in the amr claim/attribute. | For all IDPs/eIDs, one or more of: [no_bidmob, no_buypass, no_buypass:sc, no_buypass:mobile, no_buypass:pwd_otp, no_buypass:id_key:organizationName, mitid, mitid:mitid_erhverv, se_bankid, se_bankid:mobile, fi_tupas, passport_reader/ id_verifier, mobile_id, smart_id, be_cardreader, personalausweis] Here organizationName is "Buypass Id Key" issuer name provided by buypass to skip the selection page. Only for BankID (NO) and Verimi it is as below. For Verimi, one of verimi For BankID (NO), one of no_bankid |
code_challenge | The code_challenge is created by
If it is not possible to do the above transformation, the code_challenge may be set to the code_verifier value. | |
code_challenge_method | This parameter specifies the method used for the code_challenge parameter.
If the parameter is not sent in the request, IN Groupe will assign plain as the default value. | Valid values: [S256 | plain] Optional parameter in PKCE flow. |
code_verifier | The code_verifier should be a high-entropy cryptographic random string. | Format: [A-Za-zO-9-._~] Min length: 43 char Max length: 128 char Mandatory in PKCE flow. |
deflect | Where the redirect_uri should be opened. Options are to keep it in iframe (_self) or take over the page (_top). | Valid values: [_top, _self] Default: _top |
id_token_hint | ID Token parameter for prompt=none | |
max_age | Maximum Authentication Age. Specifies the allowable elapsed time in seconds since the last time the end user was actively authenticated. If the elapsed time is greater than this value, then the customer should attempt to actively re-authenticate the end user. When max_age is used, the ID Token returned should include an auth_time Claim Value. | Integer value Example: 600 for 10 minutes |
nonce | String value used to associate a client session with an ID Token, and to mitigate replay attacks. The value is passed through unmodified from the authentication request to the ID Token. Sufficient entropy must be present in the nonce values used to prevent attackers from guessing values. | Unique random value Max lenght: 500 bytes (UTF-8) |
style | A customer with a specific typographic, layout, or colour scheme can provide a URL to a CSS style sheet. If provided, the given style sheet will be used when rendering web pages in a browser. | Format: URL |
ui_locales | The language used to provide user with information during identification. If not provided, then E-Ident uses the language specified by the web browser. If no supported languages are available in the browser, or the parameter, then English is used by default. | Supported language codes: [nb-NO | nn-NO | en-GB | da-DK | sv-SE | fi-FI | sv-FI] |
wi | The wi parameter is used to indicate that the user interface shall be embedded UI. Note: The wi parameter may also be set to n to indicate standalone UI. However, as this is default UI option it is not necessary to use the wi parameter. | Valid values: [ r ] |
Mapping of eID to amr_values parameter:
ID | amr_values parameter |
|---|---|
BankID (NO) | no_bankid |
BankID (SE) | se_bankid or se_bankid:mobile |
Bank ID (FI) | fi_tupas |
Buypass (NO) | no_buypass |
MitID (DK) | mitid and/or mitid:mitid_erhverv |
Mobile-ID | mobile_id |
IN Groupe ID Verifier | passport_reader/id_verifier |
Smart-ID | smart_id |
Verimi | verimi and/or verimi:idcard |
Optional eID Specific parameters
Name | Description | Constraints | eID |
|---|---|---|---|
aal_value | Specifies the requested Authentication Assurance Level. | One of: low | substantial | high | MitID (DK) |
action_context | Specifies the action context for identification. | One of: [LOG_ON | APPROVE | CONFIRM | ACCEPT | SIGN] | MitID (DK) (Currently supported) |
acr_values | Sets the level of assurance for the identification. | Valid values: urn:eident:acrp:level:substantial urn:eident:acrp:level:high | BankID (NO), BankID (SE), MitID (DK), Finnish Bank ID (FI), Mobile-ID, Buypass, Verimi, IN Groupe ID Verifier |
amr_values | Sets the authentication method for the identification. | Valid values: For Verimi, one of verimi For BankID (NO), one of no_bankid | Verimi, BankID (NO) |
autostart | Skips first page and auto-selects BankID on this device. | Values: true | false | BankID (SE) |
cellnr8 | 8-digit mobile number for BankID on mobile (NO). | Encoding: Base64 | BankID on mobile (NO) |
dob6 | 6-digit date of birth for BankID on mobile (NO). | Encoding: Base64 | BankID on mobile (NO) |
eident_contex | Display name in app. Finnish BankID (FI): Service provider name | Base64 encoded JSON. See eID-specific page | Finnish BankID (FI) – Danske Bank, Ålandsbanken, S-Pankki, Aktia |
forcebank | Force bank selection. If not used, all configured banks will be shown. | One of: nordea | opbank | danske | aland | sbak | aktia | popbank | savingsbank | omasp | mobileid | Finnish BankID (FI) |
loa_value | Specifies requested Level of Assurance. | One of: low | substantial | high | MitID (DK) |
login_hint | Pre-selected user ID to reduce steps for user. | See login_hint description on eID-specific pages | BankID (NO), BankID (SE), MitID (DK), Mobilivarmenme (FI), Mobile-ID, Smart-ID, Verimi |
mobileid_display_text_format | Format for display text. | Valid values:
| Mobile-ID |
presetid | Pre-selected user ID to reduce steps for user. | See presetid description on eID-specific pages | BankID (NO), BankID (SE), MitID (DK), Mobilivarmenme (FI), Verimi |
reference_text | Reference text for MitID shown in the MitID app. | All characters allowed except: < >\nMax length: 130 | MitID DK |
smartid_allowed_InteractionsOrderType | Determines verification code screen behavior. | Valid values: See eID-specific page | Smart-ID |
smartid_displayText60 | Text shown in Smart-ID user app. | Max length: 60 characters | Smart-ID |
smartid_displayText200 | Text to be displayed in the Smart-ID user app. | th: 200 characters | Smart-ID |
transactiontext | Transaction text:
| Characters Max length: | |
transactiontext_type | The type of the transaction text. | Valid values: | MitID (DK) |
ntdr-app-doclist | Specifies whether to display document selection page in the mobile app for document scan i.e. to select passport or ID card. | Values: | IN Groupe ID Verifier |
ntdr-doc-issuers | Specifies which issuing countries' documents to allow during ID verification. Accepts a list of allowed document issuers (ISO 3166) country codes. | Format: [A-Za-z] | IN Groupe ID Verifier |
ntdr-doc-types | Specifies a list of accepted document types. Accepts a pattern of one or two letter document codes. | Format: [A-Za-z] | IN Groupe ID Verifier |
ntdr-expiry-grace | Enforces document validity check. If set, ID token will have failure response for expired documents. Can be positive or negative to adjust expiry grace period. | Example: 30 | IN Groupe ID Verifier |
ntdr-info | Toggle if info page to download IN Groupe ID Verifier app should be shown. | Values: | IN Groupe ID Verifier |
ntdr-facematch-min | Indicates the minimum acceptable face match level for successful authentication. | 0-9 | IN Groupe ID Verifier |
ntdr-doc-types | Allowed document types. Accepts multiple values with comma separation. | I, P, D, V (I – ID Card, P – Passport Booklet, D – Driver’s License, V – Viza/Crew credentials) | IN Groupe ID Verifier |
ntdr-app-doclist | Recommended to use. | Values: | IN Groupe ID Verifier |
ntdr-doc-issuers | Restricts the document issuer countries to the given list. | NOR for Norway, SWE for Sweden, etc (ISO-3166-1 alpha-3 cods) | IN Groupe ID Verifier |
CIBA specific parameters
Name | Description | Constraints |
|---|---|---|
amr_values | Requested Authentication Method Reference values. Can only contain a single value for CIBA transactions of all eID. But for no_bankid, this parameter contains 2 values separated by semicolon ( ; ). First value- a string that specifies the "amr" value that the Authorization Server is being requested to use for processing this Authentication Request. Second value- Comma-separated string, this will give access to control the authentication method for a specific identification. | One of: [no_bidmob, no_bankid, se_bankid, se_bankid:mobile, passport_reader/id_verifier,trustid,mitid] Second value for no_bankid, one or more of- [urn:bankid:bis | urn:bankid:bih] |
binding_message | Text to be displayed on the end user's device in text or JSON format (Base 64 encoded). |
|
acr_values | Used to set the level of assurance for the identification. | Valid values, one or more of: urn:eident:acrp:level:low, urn:eident:acrp:level:substantial, urn:eident:acrp:level:high |
Signed request
E-Ident supports Signed Request Object (Signed JWT) in OIDC requests. Both request and request_uri parameters are supported as specified by the OIDC standard. E-Ident will do a RSA signature verification to make sure that the Request Object is signed by the expected E-Ident customer by using a public key associated with the client_id.
The customer should provide IN Groupe with one of the following options for signature verification of the request parameter:
A URL to a JWKS endpoint where IN Groupe can look up a public key for signing purposes. It is optional to also provide a key id. Otherwise the first public key in the response from the endpoint will be used.
Or, the RSA key members and the key type in JSON format.
The following claims should be included in in the signed request parameter:
iss: The client that created the request.
aud: The Identity Provider the request is intended for.
Note: iss claim should be set to customer identifier (this is provided to customer by In Groupe upon registration). aud claim should be set to one of the following URLs:
For customer test: https://www.ident-preprod1.nets.eu/oidc
For production: https://www.e-ident.nets.eu/oidc
If request_uri is used, then it should be registered with In Groupe upfront.
FAQ: Traficom requirements for FTN signed authentication requests E-Ident operational information
ID Token
The ID Token is a JSON Web Token (JWT) and is either signed or signed-then-encrypted. The default is signed. For more information on encryption, see ID Token Encryption section.
The ID Token signature should be validated using the public key that is mentioned in the kid element in JWT header. The corresponding key can be looked up from E-Ident’s JWKS endpoint.
The ID Token is valid for 15 minutes. Successive token requests with the same authorization code (code) will result in error and invalidation of previously accessed tokens.
scope parameter value from the identification request. The openid value must always be used while cert, profile and ssn is optional. All ID Token claims are listed here, sorted by the scope value. See examples in Step 3 on how to retrieve an ID Token.
openid
Claim | Description | Value/Constraint |
|---|---|---|
aal | Authentication Assurance Level | One of Applicable eID: MitID (DK) |
action_context | Specifies the action context for identification | One of: [LOG_ON | APPROVE | CONFIRM |ACCEPT | SIGN] Applicable eID: MitID (DK) (Currently supported) |
acr | The level of assurance for the specific identification. | Possible values are listed on the eID pages, which will be one of: [ urn:eident:cert:eidas:high| urn:eident:cert:eidas:substantial| urn:eident:cert:eidas:low ] |
additional_info | The value of the additional info parameter if used. | |
amr | Auth Method Ref. JSON array of strings that are identifiers for authentication methods used in the authentication. In E-Ident, this is the eID type used in the identification. | One of: [no_bankid | no_bidmob | no_buypass | mitid | se_bankid | fi_tupas | fi_mobiilivarmenne | passport_reader/id_verifier | email | idcard | smart_id | mobile_id ] |
aud | Audience(s) that this ID Token is intended for. | The unique customer identifier value. |
auth_time | Time when the end user identification occurred. | The value is a JSON number representing the number of seconds from 1970-01-01T0:0:0Z as measured in UTC until the date/time. |
bp_id_sub | Unique identifier from Buypass | Applicable eID: |
bp_pid | Personal identifier of Buypass user | Applicable eID: |
card_number | Card number of the end user | Applicable eID: |
card_expiry_date | Expiry date of the end user's card | Applicable eID: |
exp | Expiration time on or after which the ID Token must not be accepted for processing. | The value is a JSON number representing the number of seconds from 1970-01-01T0:0:0Z as measured in UTC until the date/time. |
fi_trx_code | Unique but transient anonymous identifier for the end user. Remains the same in identity token and UserInfo responses during one authentication session, but is different in subsequent authentications of the same user. | Applicable eID: Mobiilivarmenne (FI) |
fi_tupas_bank | The user’s bank used in the identification process. | One of: [nordea | opbank | danske | aland | sbank | aktia | popbank | savingsbank | omasp | mobileid] Applicable eID: Finnish Bank ID (FI) |
fi_tupas_pid |
A fixed identifier for the user set in the E-Ident / FTN service. | Applicable eID: Finnish Bank ID (FI) |
ial | Identity Assurance Level | One of Applicable eID: MitID (DK) |
iat | Time at which the JWT was issued. | The value is a JSON number representing the number of seconds from 1970-01-01T0:0:0Z as measured in UTC until the date/time. |
identity_type | Type of identification | Possible values are:
Professional indicates Erhverv user Applicable eID: |
iss | Issuer Identifier for the Issuer of the response. | E-Ident issuer URI: Customer test: https://www.ident-preprod1.nets.eu/oidc Production: https://www.e-ident.nets.eu/oidc |
loa | Level of Assurance | One of Applicable eID: MitID (DK) |
mitid_amr | The list of authenticators used to achieve the resulting level of assurance for a MitID identification. | Possible values for MitID are:
Possible values for MitID Erhverv are:
Applicable eID: MitID (DK) |
mitid.uuid | Unique identifier for MitID. | Applicable eID: MitID (DK) |
mobileid_pid | Unique identifier of user in the E-Ident service. | Applicable eID: |
nemlogin.ial | Identity Assurance Level for Erhverv user | One of Applicable eID: MitID (DK) |
nemlogin.persistent | MitID Erhverv’s Global UUID/ID from EIA | Applicable eID: |
no_bid_pid | Norwegian BankID personal identifier. | Applicable eIDs: BankID (NO) and BankID on mobile (NO) |
nonce | String value used to associate a Client session with an ID Token, and to mitigate replay attacks. The value is passed through unmodified from the Authentication Request to the ID Token. | |
notafter | Certificate validity end time. | Applicable eIDs: BankID (NO), BankID (SE) |
notbefore | Certificate validity begin time. | Applicable eIDs: BankID (NO), BankID (SE) |
phone_number | 8-digit mobile/cell number (provided by merchant or user) | Applicable eID: |
pid | Personal identifier. Content will vary from eID to eID. | See possible values in "Information about end user" section for each eID. |
reference_text | Reference text from | Applicable eID: MitID (DK) |
se_bid_securitylevel | Swedish BankID security level | Applicable eID: BankID (SE) |
smartid_inter-action_flow_used | This value returns information about the type of Smart-ID interaction flow that was used. This can be one of:
| Applicable eID: |
smartid_pid | Unique identifier of user in the E-Ident service. | Applicable eID: |
sub | Subject Identifier. | A string in the format "eID type:ID" |
transaction_text | The transaction text sent through E-Ident is returned in this claim. | Applicable eID: |
transaction_te-xt_sha256 | Base64 encoded SHA256 digest of the MitID transactiontext identity provider parameter. | Applicable eID: |
transaction_te-xt_type | The type of the transaction text. This may either be html or text. | Applicable eID: |
Jti | JWT ID | The unique transaction ID |
authentication_result | Authentication result | Applicable eID: |
result_explanation | result_explanation | Applicable eID: |
chip_clone_detection | Status of chip clone detection | Applicable eID: |
facematch_level | Face match level | Applicable eID: IN Groupe ID Veriifer |
issuing_country | Issuing country (country code) | Applicable eID: |
interpreted_issuing_country | Issuing country (country name) | Applicable eID: |
cert
Claim | Description | Value/constraint |
|---|---|---|
c | The country associated with the end user's eID. | Applicable eID: All (if available) |
certificate | The end user's certificate. | Applicable eID: BankID (NO), and BankID (SE) |
certpolicyoid | The certificate policy of the end user's certificate. | Applicable eID: All (if available) |
cn | The common name from the end user's certificate. | Applicable eID: All (if available) |
dn | The distinguished name from the end user's certificate. | Applicable eID: All (if available) |
smartid_certificate_level | See description at Smart-ID page. | Applicable eID: |
Claim | Description | Value/constraint |
|---|---|---|
The end user's e-mail address. | Applicable eIDs: Verimi. | |
email_verified | This claim tells if the e-mail address has been verified or not. | One of: true | false Applicable eIDs: Verimi |
nemid.pid
Claim | Description | Value/constraint |
|---|---|---|
nemid.pid | If the user has a NemID identity, this will be the user's unique NemID PID value. | Applicable eIDs: MitID |
organisation
Claim | Description | Value/constraint |
|---|---|---|
authorized_to_represent | The organisation number (Danish CVR number) the user has selected and is authorised to represent. The user can select a company when using the Private MitID - on behalf of companies functions. | Applicable eID: |
organisation_name | Private MitID: The name of the organisation the user logs in on behalf of. For Finnish Bank ID: | Applicable eID: |
organisation_number | For MitID: The organisation number received when using the Private MitID - on behalf of companies function. For Finnish Bank ID: | Applicable eID: |
phone
Claim | Description | Value/constraint |
|---|---|---|
phone_number | The end user's phone number. | Applicable eIDs: Mobiilivarmenne (FI) and Verimi |
phone_number_verified | This claim tells if the phone number has been verified or not. | One of: true | false Applicable eIDs: Verimi |
profile
Claim | Description | Value/constraint |
|---|---|---|
birthdate | Date of birth in the format DD.MM.YYYY | Applicable eID: BankID (NO), Finnish Bank ID (FI) and Mobiilivarmenne (FI), AusweisApp |
family_name | The end user's surname | Applicable eID: All (if available) |
given_name | The end user's given name. | Applicable eID: All (if available) |
name | The end user's full name. | Applicable eID: All (if available) |
nemlogin.age | Age of Erhverv user | Applicable eID: MitID (DK) |
nemlogin.auth_to_repr | CVR number of the Organisation for which the MitID user is authorized to represent. | Applicable eID: MitID DK) |
nemlogin.cpr_uuid | Unique ID for Erhverv user | Applicable eID: MitID (DK) |
nemlogin.cvr | Company CVR for Erhverv user | Applicable eID: MitID (DK |
nemlogin.date_of_birth | Date of birth for Erhverv user | Applicable eID: MitID (DK) |
nemlogin.email | Email address for Erhverv user | Applicable eID: MitID (DK) |
nemlogin.family_name | Family name for Erhverv user | Applicable eID: MitID (DK) |
nemlogin.given_name | Given name for Erhverv user | Applicable eID: MitID (DK) |
nemlogin.name | Full name of Erhverv user | Applicable eID: MitID (DK) |
nemlogin.nemid.rid | Employee certificate RID from NemID migration (or assigned) | Applicable eID: MitID (DK) |
nemlogin.org_name | Company name for Erhverv user | Applicable eID: MitID (DK) |
nemlogin.p_number | Company P number for Erhverv user | Applicable eID: MitID (DK) |
nemlogin.persistent | MitID Erhverv’s Global UUID/ID from EIA | Applicable eID: MitID (DK) |
nemlogin.se_number | Company SE number for Erhverv user | Applicable eID: MitID (DK) |
auth_files_url | A URL to download authentication files. Read more about the authentication files. | Applicable eID: IN Groupe ID Verifier |
document_number | The Document Number | Applicable eID: |
document_type | The Document Type | Applicable eID: |
place_of_birth | Place of Birth | Applicable eID: Verimi IDCard IN Groupe ID Verifier, AusweisApp |
date_of_expiry | Date of Expiry of the document | Applicable eID: Verimi IDCard IN Groupe ID Verifier, AusweisApp |
citizenship | Citizenship of the end user | Applicable eID: Verimi IDCard |
issue_date | The Document issue date | Applicable eID: Verimi IDCard |
issuing_authority | The Document issuing authority | Applicable eID: Verimi IDCard |
verification_method | Verification Method | Applicable eID: Verimi IDCard |
verification_date | Date of verification | Applicable eID: Verimi IDCard |
gender | Gender | Applicable eID: |
nationality | Nationality (country code) | Applicable eID: |
interpreted_nationality | Nationality (country name) | Applicable eID: |
primary_identifier | Predominant componet of | Applicable eID: |
secondary_identifier | Secondary component of | Applicable eID |
authentication_sources | This claim provides information on which data sources have been employed to produce an authentication or ID verification. | Possible values: Any combination of SDK_NFC, SDK_FACESCAN, REMOTE or SDK_OCR. Applicable eID: |
other_identifier | This claim provides all names that could not fit in the primary identifier, either due to size constraints, or character encoding such as diacritics. This claim is to convey subject names not included in the primary and secondary identifier claims. | Applicable eID: |
ssn
Parameter | Description | Value/constraint |
|---|---|---|
dk_ssn | Danish SSN | Applicable eID: MitID (DK) |
fi_ssn | End user's Finnish personal identity code (henkilötunnus). | Applicable eIDs: Finnish Bank ID (FI) and Mobiilivarmenne |
fi_satu | Finnish unique identification number (sähköinen asiointitunnus). | Application eID: Finnish Bank ID (FI) |
no_ssn | Norwegian SSN | Applicable eID: BankID (NO), and Buypass |
se_ssn | Swedish SSN | Applicable eID: BankID (SE) |
smartid_document_number | See description at Smart-ID page. | Applicable eID: |
ssn | Social security number / National identifier | Applicable eIDs: BankID (NO), Buypass (NO), MitID (DK), BankID (SE), Finnish Bank IDs (FI) and Mobiilivarmenne. |
ssn_issuing_country | The country that issued the user's ssn. | Currently supported: |
personal_number | The value stored in the personal_number field in the passport/id card. Value is as defined by document issuer, can be SSN, or similar. | Applicable eID |
address
Claim | Description | Value/constraint |
|---|---|---|
address | The end user's address | Applicable eIDs: Mobiilivarmenne (FI) and Verimi, AusweisApp |
ageverifyxx
Claim | Description | Value/constraint |
|---|---|---|
age_verified | This claims tells if the age has been verified or not | One off: true | false | inconclusive Applicable eIDs: Finnish BankID (FI) |
age_verificaion | Returns the value as ageverifyxx where xx denotes the age to be verified | Applicable eIDs: Finnish BankID (FI) |
ID Token samplerd
.xml
{
"sub" : "mitid:PID:xx-xx-xx-xx",
"dk_ssn" : "xx",
"amr" : "mitid",
"mitid.uuid" : "xx-xx-xx-xx",
"iss" : "https://www-ident-test.nets.no/oidc",
"dn" : "CN=Frida Jørgensen",
"pid" : "PID:xx-xx-xx-xx",
"nonce" : "nonce07/06/2023",
"aal" : "https://data.gov.dk/concept/core/nsis/High",
"ssn" : "xx",
"aud" : "MER2",
"ial" : "https://data.gov.dk/concept/core/nsis/High",
"mitid_amr" : [ "code_app" ],
"exp" : 1686117229,
"identity_type" : "private",
"iat" : 1686116329,
"jti" : "xx-xx-xx-xx-xx",
"loa" : "https://data.gov.dk/concept/core/nsis/High"
}
ID Token encryption
Customers can request IN Groupe to encrypt all ID Tokens. The ID Token will be encrypted using RSA-OAEP-256 and AES, as described by RFC 7516. JWE Compact serialization is used and the encryption is done after signing, which means that the customer needs to decrypt the ID Token before being able to validate the signature.
The customer will need to provide IN Groupe with one of the following options:
A URL to a JWKS endpoint where IN Groupe can look up a public key for encryption purposes. It is optional to also provide a key id. Otherwise the first public key in the response from the endpoint will be used.
The RSA key members and the key type in JSON format.
Note: The use of encrypted ID Token is required for Finnish Trust Network customers offering identification with Finnish Bank IDs and Mobiilivarmenne.
Get in touch with support for more details Contact Support
OIDC discovery URL
OIDC discovery request has to be made to get the token_endpoint and jwks_uri. This can be done programmatically or manually to get the token_endpoint uri and jwks_uri.
The OIDC discovery URL:
Customer test: https://www.ident-preprod1.nets.eu/oidc/.well-known/openid-configuration
Production: https://www.e-ident.nets.eu/oidc/.well-known/openid-configuration
OIDC UserInfo endpoint
The UserInfo endpoint returns claims about the authenticated user, including some claims not available in the ID token. Accessing this endpoint requires an access token. This token is returned together with the ID token. The access token shouldn't be expired to get the authentication data. The endpoint response will be signed by default and encrypted optionally.
For SAML protocol, the access token will be available in the SAML response.
The OIDC userinfo endpoint URL:
Customer test: https://www.ident-preprod1.nets.eu/oidc/userinfo
Production: https://www.e-ident.nets.eu/oidc/userinfo
Requesting authentication data from UserInfo endpoint
.sh
curl https://www.ident-preprod1.nets.eu/oidc/userinfo -H "Authorization: Bearer <<access token>>"
Sample UserInfo endpoint response after decoding and/or decrypting the response
JavaScript
{
"sub" : "se_bankid:xxxxxxxxxxxx",
"user_signature" : "<<user_signature>>",
"user_cert_ocsp" : "<<user_cert_ocsp>>",
"notbefore" : "20210112230000",
"amr" : ["se_bankid"],
"notafter" : "20230113225959",
"iss" : "https:\/\/www.ident-preprod1.nets.eu\/oidc",
"given_name" : "Test",
"nonce" : "nonce06\/09\/2021",
"auth_device_ip" : "xxx.xxx.xxx.xx",
"ssn":"xxxxxxxxxxxx",
"access_token" : "QzLCDFodNn0y4XdGY2AVKRdDxY2JFiHLDZm0bz8aV-E",
"aud" : "Test merchant",
"se_ssn" : "xxxxxxxxxxxx",
"name" : "Test Testesen",
"exp" : 1630915131,
"iat" : 1630914231,
"family_name" : "Testesen",
"jti" : "278b78056a8349f68be8679d7f908159"
}
Userinfo endpoint claims
The userinfo endpoint may return these claims in addition to the claims in the ID Token.
Claim | Description | Value/Constraint |
|---|---|---|
picture | Picture of the end user as read from the card | Currently supported for
|
user_cert_ocsp | The OCSP response returned from the eID when validating the authentication. | Currently supported for:
|
user_signature | The signature returned from the eID during the authentication. | Currently supported for:
|
verification_info | Proof of authentication as provided by the electronic ID provider. | Currently supported for:
|
access_token | Credential issued by authorization server for accessing protected APIs | Supported for all eIDs |
face_scan_time | Time when face scan was | Currently supported for:
|
document_scan_time | Time when document scan was | Currenly supported for:
|
transaction_start_time | Time when the transaction was started | Currently supported for:
|
transaction_end_time | Time when the transaction was completed | Currently supported for:
|
authentication_result | authentication_result | Currently supported for:
|
result_explanation | result_explanation | Currently supported for:
|
Recommended reading
The OIDC standard is described here: http://openid.net/connect/
Referenced documentation: http://openid.net/specs/openid-connect-core-1_0.html
Reference implementations:
